Cisco offers two quite different downloads of its Secure Client for macOS. The one most commonly used by Mac Admins is the “predeploy”. Cisco Secure Client is now a suite of security agents. There are now ten components installed by default when using a predeploy package from Cisco. However, it is doubtful that an organization would be deploying all ten.
With each release of Cisco Secure Client (and AnyConnect before that), there has been a cat and mouse game process of discovering the new components and how to exclude them from one’s custom install. We not only need to customize the installation but need to do it reliably and repeatedly as additional default components are added.
Customizing what components are installed is via a “choice changes XML” file. A file can be generated for a given package usinginstaller -showChoiceChangesXML -pkg /path/to/file.pkg
A choice changes file is a Property List (plist), which is just a particular XML schema. macOS has many built-in plist and XML tools, so I reckoned it was possible to interrogate the output of -showChoiceChangesXML for all possible valid choices, and then loop back through them to build a choice changes XML that only selected the desired components.
An alternative
Additionally, I wanted to explore an alternative to the predeploy package. As suggested to me by David Cohen on MacAdmins Slack, the webdeploy package contains macOS installer packages for individual Cisco Secure Client components1. Having worked in IT Security prior to being a Mac administrator, I was familiar with the webdeploy and its intended purpose. Ordinarily, a VPN administrator would put a webdeploy package on a Cisco VPN gateway, like an ASA, to update clients as they connect to the VPN. While it has a .pkg file extension, it isn’t a macOS installer package but a highly structured zip file. Amongst the unzipped contents one will find disk images for individual components.
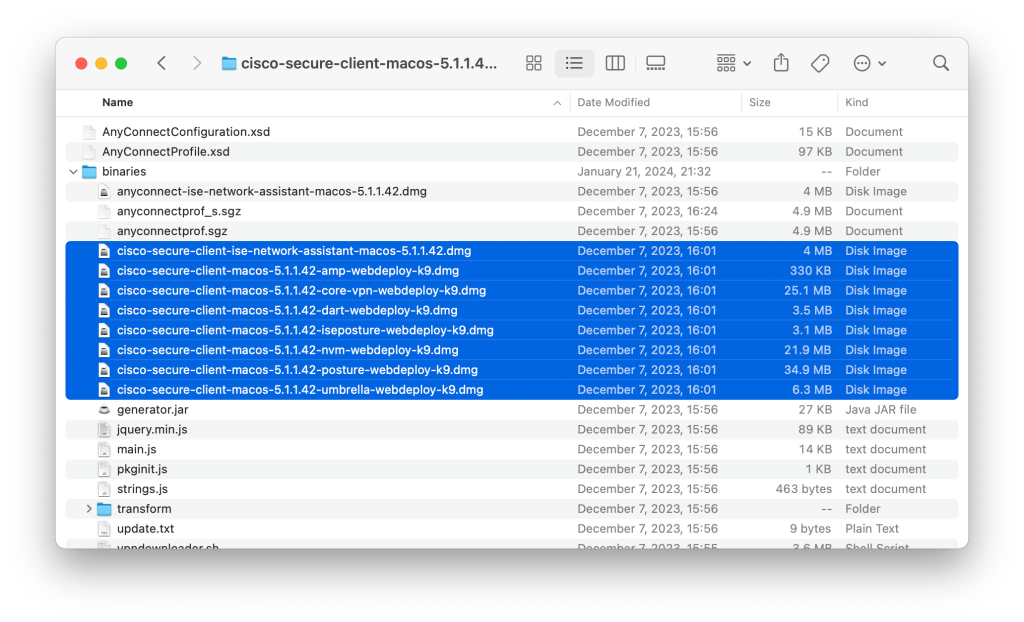
In each disk image is a macOS installer package. Digging out each package individually is a chore, but the webdeploy file is intended for automation: it is structured so that automatic updates can occur.
Automation for building custom installers
The result of this exploration is two scripts, one for predeploy and another for webdeploy. While they have slight differences based on the source they are customizing, both build disk images for an organization with only the desired components. Save that nothing else changes, Cisco could add another ten components to Secure Client and these scripts would continue build disk images for only the desired set of components.
The resulting disk images, and the packages inside, still have to be deployed using a management system. But these scripts have removed the work from making a custom Cisco Secure Client installer.
(More options, such as disabling VPN and adding profiles, are documented in the README.md file in GitHub.)
| Predeploy advantages | Webdeploy advantages |
| Simpler, single package | Smaller download size |
| Cisco’s preferred option | |
| All components available |
- This is functionally similar to how Cisco packages the Secure Client predeploy for Windows: individual Windows Installer files (.msi) for each component. ↩︎
Leave a comment